Cscan
Good afternoon, Friends, Dear Forum users and of course, Dear Readers and Residents of the Forum.
For a long time I could not publish reviews, I confess.
I will allow myself a short digression from the review (you can skip the paragraph)
There were reasons for that, but I have nothing to hide before you and the Brothers.
(I hacked not what I needed for work and instead of cutting off my head I was invited to administer what I had)
(Knowledgeable guys from the Forum were in touch with me at this time, for which a special Thank you.)
As always, the Forum supports and does not let its Residents.
My work is now scheduled according to the schedule. While at home on vacation. And I can afford articles on the Forum.
The presence at the Forum from time to time before this time thanks to someone else's Internet, which was forgiven (well, you understood correctly).
From the server, which is now assigned to me, I cannot conduct my experiments during my official duties. (please understand).
So, by tradition, I am introducing you to pentesting tools from Asia.
I would like to introduce you to a pentester from Asia under the nickname j3ers3.
And the first tool developed by the author is Cscan.
Cscan is designed to scan a network by mask and domain.
It shows open ports and what is hosting hosting.
Yes, this does not replace the Nmap scanner (this monster has no equal yet).
But when other scanners are silent, this one can be useful to you.
I'm not talking about downloading it, just for information, it can help you out.
The BlackArch distribution kit often helps me in the review, at last it is with me now.
Tool installation:
The code:
# git clone https://github.com/j3ers3/Cscan.git
# cd Cscan
# chmod +x cscanV2.py cscanV1.py
# pip3 install -r requirement.txt
# python3 cscanV2.py -h команда справки
The code:
# python3 cscanV2.py -i ip_адрес/24 -t 100
The code:
# python3 cscanV2.py -f domain.txt -t 100Which we will not harm, nevertheless.
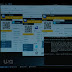
The options can be seen on the main screen.
Then we go, we basically have port 445
open. It is actually responsible for working with shared files in windows without connecting netbios.
But as luck would have it, not this time (there are exceptions).
Ip addresses will be retouched to comply with ethics.
Hosts protected by Cloudflare
Look further
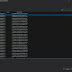
About the results now:
Port 3306 is a Mysql
port Port 1433 TCP data transmission control protocol
Port 1434 is a Microsoft Sql server, but it also hangs on a different IP.
Also port 1521 -Oracle database appears, and unspoken, there is food for thought, but not this time.
In addition, there are open ports 3306-Database Management System MySQL
3389-Microsoft Terminal Server (RDP) Officially and other ports.
Yes, this is a tasty resource for pentesting, but only that stopped it: Linux
Host, not the one we were looking for, unfortunately, but running Linux Debian, which sharply precipitated the ardor and bloodlust.
(you have to respect the Brothers and Linux)
There is a version of Apache for which you can search for vulnerabilities.
That's all for now, see you soon.
Take care of yourself and thank you for your attention.








Commentaires