How to intercept accounts of social networks, mail and personal information via Wi-Fi using Android.
All the described information carries only the educational element, and has no call to action. The author does not bear any responsibility for the possible application of the knowledge gained in practice. Remember, access to confidential information of people without their consent is illegal, and generally uncivilized. Be prudent.
A small preface.
How often do you connect to public networks? I bet it is not always possible to “throw” money on your phone, but the need to connect to the Internet always exists.
Imagine you are driving in a trolleybus, and you are in correspondence with your other half. And at one point you suddenly end up with available traffic. Unfortunately, there is nowhere to refill an account in a trolleybus, but there is always public Wi-Fi! If you are not particularly concerned about the security of your data, feel free to connect to it and continue to exchange emoticons with your beloved or beloved one. However, if your privacy is important to you, it makes sense to continue reading this article, because if you have a smartphone with Root rights, each one can simply steal your social network account, or get access to your mailbox.
T Thetheoretical part.
Data exchange on the Internet is encrypted. In this article, we are not interested in how data packets are sent from the user to the web server. We are more interested in the return path of datagrams to the user. So, after processing the HTTP request, the server checks if the client has the right to use the GET request, and if the answer is positive, the server finds the content requested by the client, encrypts it into a packet, and sends the result back using PHP.
A thief of information cannot use a GET request, since only a person who possesses the necessary information has access to it (in the case of a social network, this is a login and password). However, a hacker doesn’t always need to send a GET request - it’s enough for a person who is on the same subnet to do it. This subnet in this case is the Wi-Fi network.
The cracker only needs to “pick up” the incoming data packet at the right time, which in any case passes through the subnet, write the cookie, and the trick is done. For this kind of hacking and there is cSploit for Android.
KHow does this happen in practice.
So, a brief excursion into the program. Officially, cSploit is used to analyze the Wi-Fi network for security, but we will consider a slightly different application of the program. But only within the law.
Attention!
The program requires Root rights and the BusyBox libraries. I hope there should be no problems with their installation.
Now that we know in more detail how and when the user receives data from the server, it is time to consider how to capture them using Sploit.
AndInstruction.
- Install Root rights, as well as BusyBox.
- Download cSploit, and also install it on your smartphone.
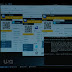
- If the first two steps were performed correctly, when you start the application and connect to Wi-Fi, you will see all devices connected to the network.
- Next, you need to select the "victim" and tap on it once.
- Before you appeared a lot of interesting modules to influence the selected device, but we are interested in the section MITM (man-in-the-middle). Choose it.
- Next, select the section "session sniffer". I see no reason to explain what it is, because the name speaks for itself J
- Now, if you know the victim personally, you can through social. engineering to "convince" him that he urgently needs to go to his "Contact", or wait until he does it himself.
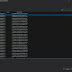
- At the moment when the victim enters his account - on your smartphone in the list of intercepted sessions there will be a new, often named simple IP session, which must be intercepted.
- We make the interception with a simple tap and confirmation.
- Profit! The browser opens with the victim's page. Now you can make changes to the victim's account, read and write messages, as well as upload photos (for example).
As you can see, for hacking it is not necessary to have extensive knowledge in the field of programming, to belong to Anonymous, or to have a cool hacker software for a couple with powerful devices . Each child with proper skill can turn such a simple business, that is why the purpose of this article was not to raise a new generation of hackers, but to warn about the possible danger of your data.
Be alert, careful, and do not post too much information about yourself on the Internet.
Good luck to all!







Commentaires